Manage application users
Overview
The Participants page in RiskStudio is your central hub for managing individuals within Organizational Units involved in your organization's risk management efforts. It provides a clear overview of roles, responsibilities, and permissions, facilitating effective collaboration and improving the efficiency of risk management activities. This guide will help you navigate and use the Participants feature to optimize teamwork and streamline risk management workflows.
Participant Management
The Participants section is crucial for aligning everyone involved in your risk management processes with your cybersecurity goals. Here, you can view, manage, and organize participants, ensuring everyone is on the same page for effective risk mitigation.
Participant overview: This page lists all participants involved in your risk management activities, including their names, email addresses, company affiliations, roles, and additional notes. You can edit participant information, assign roles, and invite new participants to join the workspace.
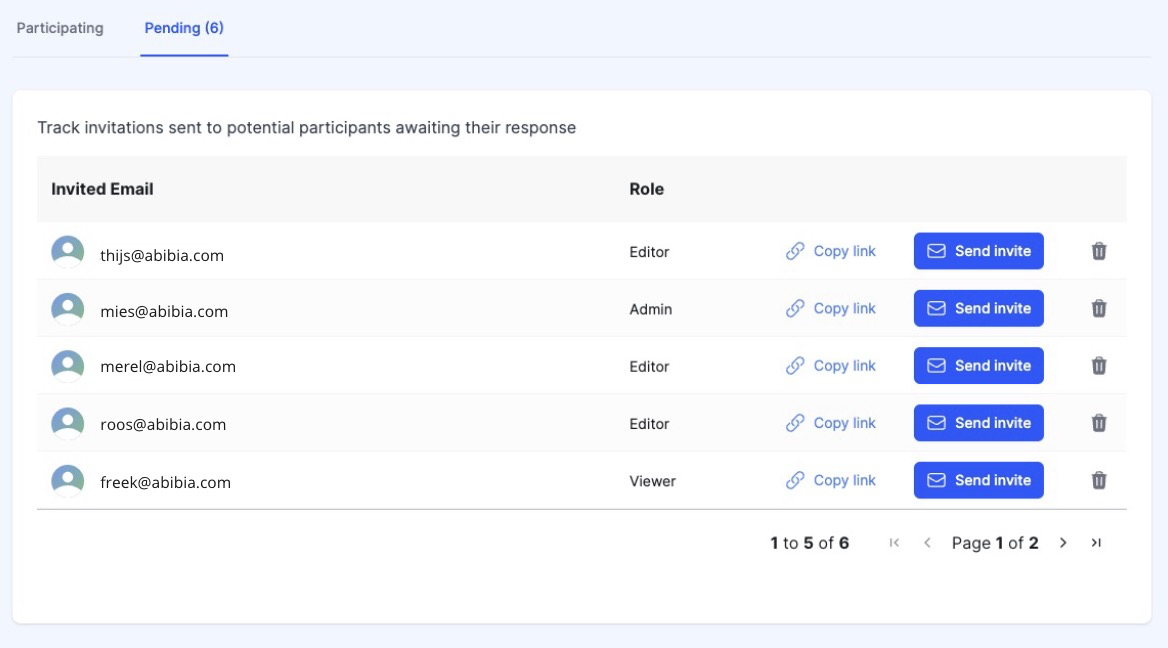
Pending Invitations: The Pending tab provides a list of participants who have been invited but have not yet joined. You can resend invitations, generate access links, or revoke pending invites to manage the onboarding process effectively.
Inviting Participants
Inviting participants to RiskStudio is simple. Use the Invite Participant button to fill in participant details, assign roles, and choose whether they will have access to the workspace or be added as a contact only. The invitation is sent directly to the participant's email, ensuring a smooth integration process.
Assigning Roles and Permissions
Roles and permissions are key for managing participants effectively. RiskStudio allows you to assign roles such as Admin, Editor, Viewer, or Guardian, each with different levels of access.
Meer informatie over de rollen is terug te vinden in de sectie How it works - Roles & Permissions.
Contacts vs. Workspace Users: Contacts are individuals added without workspace access, primarily as external references. Workspace Users, on the other hand, have active roles with specific permissions within the workspace. Assigning the appropriate role helps maintain control over access and responsibilities.
Event Triage Access: For Editor and Viewer roles, you can grant access to the Event Triage feature, which allows them to contribute to incident management. Admins and Owners have access to this feature by default.
Tips for Getting Started:
Begin by inviting key participants and assigning appropriate roles to ensure they have the right level of access.
Use the Participant Listings to keep track of everyone's role and ensure that the correct permissions are assigned.
Regularly review pending invitations and resend or revoke as needed to maintain an accurate participant list.
