Attack Surfaces
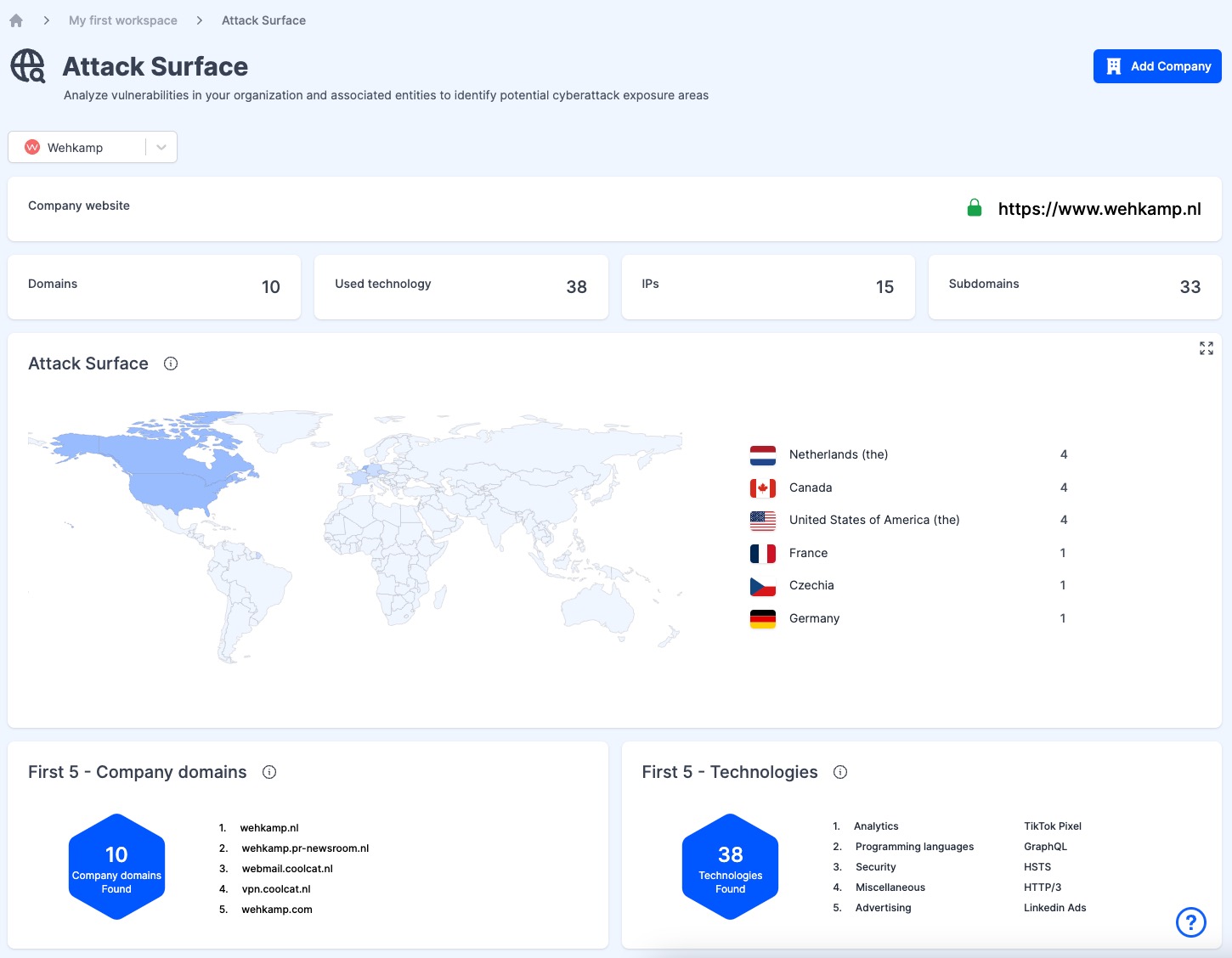
Attack Surfaces main screen
1. Introduction
Attack Surfaces are the numerous points where an unauthorized user can try to enter data or extract data from an environment. Recognizing and understanding these surfaces is pivotal in ensuring optimal cybersecurity. RiskStudio's 'Attack Surfaces' tool provides a detailed overview, allowing you to visualize and manage these vulnerable points within your digital ecosystem.
2. Functionalities
From the main menu, navigate to 'Control' and then select 'Attack Surfaces'.
On the 'Attack Surfaces' page, you can explore and analyze the digital vulnerabilities of every company within your Cyber Chain. This interface allows for an in-depth assessment of potential cyber threats associated with these entities.
2.1 Select a Company
Select a company from the dropdown list to view its specific attack surface details. Easily add companies not yet in the Cyber Chain list with the ‘Add Company button’, enhancing your cybersecurity coverage.
For more information on adding, modifying, deleting and archiving Cyber Chain Companies, see the page Cyber Chain Companies.
After selecting a Company from the dropdown list, you will see the following Attack Surface details:
2.2 Company Website
Displays the primary website of the selected company, serving as a starting point for assessing online vulnerabilities.
2.3 Domains
Shows the total number of domains associated with the selected company. The total number of domains indicates the breadth of a company's online presence, which is crucial for assessing the scope of digital risk exposure and potential attack vectors.
2.4 Used Technology
Indicates the number of different technologies utilized by the company, which can be potential vectors for cyber threats. Knowing the variety of technologies a company uses is essential for identifying potential cybersecurity vulnerabilities and planning appropriate defensive strategies.
2.5 IPs
Lists the total number of IP addresses linked to the company, highlighting its digital footprint. The count of IP addresses associated with a company helps in mapping its digital footprint, essential for understanding its internet exposure and potential for targeted cyber attacks.
2.6 Subdomains
The number of subdomains under the company's main domain, each a potential point of vulnerability. Subdomains represent additional points of digital entry, each potentially vulnerable, making their identification vital for a comprehensive cyber risk assessment.
2.7 World Map with Server Locations
An interactive map showing the geographical distribution of the company’s servers, providing insights into global exposure. The geographic distribution of servers can reveal risk factors like geopolitical instability or data sovereignty issues, influencing global cybersecurity strategies.
2.8 Company Domains Found
A comprehensive tally of all domains associated with the company provides valuable insights into its digital reach, complexity, and the extent of potential cyber exposure.
2.9 First 5 Company Domains
Highlighting the most prominent domains of a company helps prioritize risk management efforts on the most significant and potentially vulnerable digital assets.
2.10 Technologies Found
Understanding the total range of technologies in a company's infrastructure is key to identifying both known and emerging cybersecurity threats.
2.11 First 5 Technologies
Focusing on the primary technologies used by a company allows for targeted risk management and the strengthening of defenses in critical areas of potential vulnerability.
3. Maximizing the potential of ‘Attack Surfaces’
Regularly update and review your Cyber Chain to keep the attack surface data current.
Utilize the insights gained to allocate resources effectively, focusing on guarding the most critical vulnerabilities.
4. Frequently Asked Questions (FAQs)
Q: How does RiskStudio identify Attack Surfaces?
A: RiskStudio combines automated scans, integrations with your existing systems, and industry best practices to identify potential attack surfaces.
Q: How frequently should I review the Attack Surfaces?
A: Regular reviews are crucial. It's recommended to check your Attack Surfaces after any significant changes to your systems or at least on a quarterly basis.
